This article gives a brief overview of how a small business firewall server is setup and configured. It includes principles that apply to any small business setup. Brought to you by Mark Rais.
I will assume that you’re reading this because you need to understand how the basics of how a small business Linux firewall works. If you also need more information regarding actual configuration of a firewall using IPTables, please read Linux Firewalls using IPTables. Now let me start briefly with the essentials for firewalls and Linux security.
- A stand alone Linux PC (not dual booting and only used for firewall)
- Two 10/100 Ethernet cards installed in the PC
- A DSL or Cable modem and established ISP account and connection
- Basic multi-port workgroup hub (aka. network switch)
• Linux flavor of your choice with as few applications running as possible except for basic firewall and networking tools
• You should at least understand the following diagram to be able to configure your particular flavor’s firewall and hardware settings:
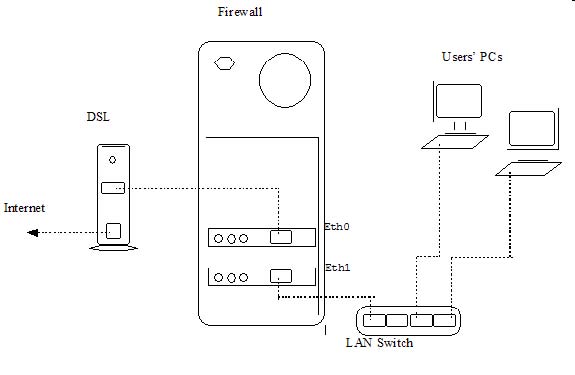
Fedora Business Firewall Overview
The most important thing to remember before you begin investigating the solution is that two ethernet devices need to be independently configured.
Ensure that both of your ethernet devices are properly configured and set active using the Activate button. One device, in my case eth1 is set to handle DHCP. The other device, eth0, is set to a static IP address. In this way, you create the proper hardware setup to enable two very key ingredients to a working firewall router. The two key ingredients are: packet forwarding and IP masquerading.
I am a pragmatic and very impatient Linux user. For this reason I will tell you the summary of what you would need to take if you were to manually configure Fedora for firewall routing, but I can not recommend this when there are other reasonable solutions.
The hard way, for those who care to know, is to modify the file called /etc/sysctl.conf. The sysctl is used to manually configure kernel parameters when the server boots up. Whether someone who is a beginning Linux user actually want to tinker at this level is questionable. Next you would need to set IP Masquerading with a specific command so long that my book editors could not devise a tiny enough font setting for it! You must enable the /sbin/iptables for your two ethernet devices.
It is not a process I recommend, and therefore not a process I include in this basic overview chapter on business firewall configuration.
If you still prefer to manually configure the IPTables then I suggest you review the Linux IP Masquerade HOW-TO by David Ranch found on the internet, which does a thorough job of summarizing the concept. The document refers to 2.4.x kernels but most of the information still applies. Today, the latest Fedora kernel will allow this through existing IPTables configuration. You should also review the Fedora forums on the subject.
So what do I recommend for Fedora users who need a solid and useful firewall configuration tool? My personal preference is to use Firestarter by Tomas Junnonen and help from others including Paul Drain.
This is one of a number of very good firewall configuration tools available on the internet. Ultimately, the choice is yours to make based on budget, time, and interest in how much about the IPTables file and configuration you really care to know.
Before you start, ensure that your two interface devices are properly configured. Thankfully, SuSe includes an easy interface for making changes to your ethernet cards under the YaST tool.
In the Firewall settings module of SuSe’s YaST, ensure that when you have the option to select devices, you choose the two applicable independent devices, not just one.
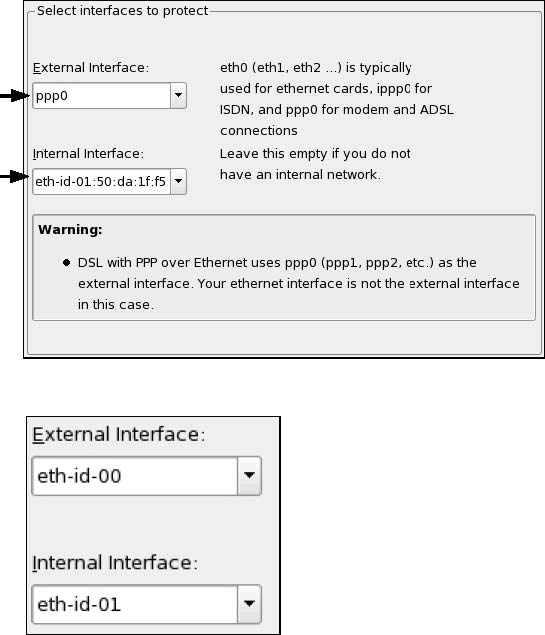
Sometimes, depending on your modem setup, you must instead select the ethernet card id as shown in the second image.
What allows your firewall to be secure for inbound connections is the operation of masking the internal IP addresses while accepting the DHCP address given through the modem connection by your ISP.
To configure the internal network you will need to control the TCP internal network addresses by assigning a static IP to the Eth1 device and allowing DHCP for the Eth0 (ppp) device.
Be sure during the configuration that the Forward Traffic and Do Masquerading is selected and Allow Traceroute is unselected.
Once you’ve saved your firewall settings and gone back to stop any unneeded processes, your basic business firewall is ready. I always recommend that at this point, before actually connecting internal PCs to the firewall server, you take time to review available Linux security updates and information on the web. Your flavor’s website and other excellent news and information sites including linux.com and linuxtoday.com will have updated flavor specific security information.
Please do not connect your business to the internet until you have taken some time to review security information for your specific flavor. It’s part of being a good system administrator, and I highly recommend it.
Another key aspect of proper system security and firewall setup is a rou tine check on your system logs. The logs will help identify strange in- bound process requests, hack attempts, and other potential threats.
You’re going to need to become very familiar with your logs if you plan to succeed as a business server administrator.
For Fedora and SuSe, the system logs are usually found under: /var/log/messages /var/log/secure
You can quickly review the logs by reading them directly in the shell with commands like: tail /var/log/messages
This will print the most recent 10 log entries for your server.
And please remember, this is only your system log. You will have other
logs such as the ones generated by the http daemon for all web server re-
sponses. Logs, though annoying, are very helpful in diagnosing security
vulnerabilities and issues.
You may also benefit from reading this article on Beginner Server Administration.